 Google Hacking for Penetration Testers
Google Hacking for Penetration Testers
…multiple live security camera views… …and historical records of recorded video feeds. Even doofus hackers know how to use default passwords to get… Thanks to.
 FREE-FALL: HACKING TESLA FROM WIRELESS TO CAN BUS
FREE-FALL: HACKING TESLA FROM WIRELESS TO CAN BUS
A Wi-Fi SSID Tesla Service
 Certified Blackhat- Methodlogy to Unethical hacking (1)
Certified Blackhat- Methodlogy to Unethical hacking (1)
know the target systems is the first process in ethical hacking. Social such as an e-mail attachment or pdf and has the ability to make its. “signature ...
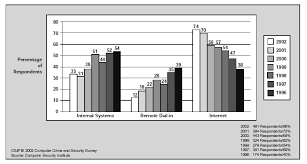 Black Hat
Black Hat
to learn a certain number of MAC addresses per port. Upon detection of an invalid MAC the switch can be configured to block only the offending MAC or just
 Hacking Serverless Runtimes Profiling Lambda Azure
Hacking Serverless Runtimes Profiling Lambda Azure
https://www.blackhat.com/docs/us-17/wednesday/us-17-Krug-Hacking-Severless-Runtimes.pdf
 Business Hall
Business Hall
https://encrypted-tbn2.gstatic.com/images?q=tbn:ANd9GcQhgBfCt--hmvC3xfEEDxTdL-6toGD7lwuJr7NqpOiFLnKtCbBkPAKDYYrR
 Rocking the pocket book: Hacking chemical plants for competition
Rocking the pocket book: Hacking chemical plants for competition
pdf. [34] Jason Larsen. “Miniaturization”. In: Black Hat USA (2014). http://http://blackhat.
 Hacking VoIP Exposed
Hacking VoIP Exposed
SIP extensions are useful to an attacker to know for performing Application specific attacks (hijacking voicemail brute forcing
 A Pictures Worth - Digital Image Analysis and Forensics Version 2
A Pictures Worth - Digital Image Analysis and Forensics Version 2
pdf. Page 23. N. Krawetz. A Picture's Worth... 23 of 43. Copyright 2007-2008 Hacker Factor Solutions presented at Black Hat Briefings DC 2008. Figure 23 ...
 Black Hat Go
Black Hat Go
Jun 27 2019 isn't Learning to Program Elegantly with Go—this is Black. Hat Go. WHY USE GO FOR HACKING? Prior to Go
 Making money on the Web the black hat way
Making money on the Web the black hat way
Contributing author of "Hacking. Exposed: Web Applications." 2. Page 9. © 2008 WhiteHat Security Inc. WhiteHat
 Becoming a Black Hat Hacker
Becoming a Black Hat Hacker
There are many ways you can learn computer systems programming
 Google Hacking for Penetration Testers
Google Hacking for Penetration Testers
…multiple live security camera views… …and historical records of recorded video feeds. Even doofus hackers know how to use default passwords to get… Thanks to.
 Black Hat Hacker White Hat Hacker Gray Hat Hacker
Black Hat Hacker White Hat Hacker Gray Hat Hacker
Black-hat Hackers are also known as an Unethical Hacker or a Security Cracker. These people hack the system illegally to steal money or to achieve their own
 Untitled
Untitled
“Gray Hat Hacking Second Edition takes a very practical and applied approach to learning how to attack computer systems. The authors are past Black Hat
 Top Ten Web Attacks
Top Ten Web Attacks
Net-Square. BlackHat Asia 2002 Singapore Increased —web hacking“ activity. • Worms on the web. ... OS vendors learning from past mistakes (?).
 Hacking a Professional Drone
Hacking a Professional Drone
The goal of this talk is to give insights into the security of. Unmanned Aerial Vehicles (UAVs) and to show that professional.
 Blackhat-Hacking.pdf
Blackhat-Hacking.pdf
Blackhat Hacking. How to hack and not get caught. Brady Bloxham. Silent Break Security Know your network. – That means monitor the traffic.
 $atellite Hacking for Fun & Pr0fit!
$atellite Hacking for Fun & Pr0fit!
Full Disclosure / White Hat! ? Freelance research / training / lecturing Hacking a Bird in The Sky. ? Old Skewl ... You've got to know how to grab it.
 Hacking Databases for Owning your Data
Hacking Databases for Owning your Data
Database vulnerabilities affect all database vendors I know it's old news but guess what? it's still a big issue
 Phishing with Super Bait
Phishing with Super Bait
WhiteHat Security is a leading provider of web application a URL the hacker can redirect any end user though Lycos directory to their fraudulent page.
Crackers or Malicious Hackers:
System crackers attempt to access computing facilities for which they have not been authorized. Cracking a computer's defenses is seen as the ultimate victimless crime. The perception is that nobody is hurt or even endangered by a little stolen machine time. Crackers enjoy the simple challenge of trying to log in, just to see whether it can be done. Most crackers can do their harm without confronting anybody, not even making a sound. In the absence of explicit warnings not to trespass in a system, crackers infer that access is permitted. Others attack for curiosity,personal gain, or self-satisfaction. And still others enjoy causing chaos, loss, or harm. There is no
common profile or motivation for these attackers.Classification of Hackers:
Hackers can be classified broadly into three different categories:1. Black Hat Hacker
2. White Hat Hacker
3. Grey Hat Hacker
Black Hat Hacker
Black-hat Hackers are also known as an Unethical Hacker or a Security Cracker. These people hack the system illegally to steal money or to achieve their own illegal goals. They find banks or other companies with weak security and steal money or credit card information. They can also modify or destroy the data as well. Black hat hacking is illegal.White Hat Hacker
White hat Hackers are also known as Ethical Hackers or a Penetration Tester. White hat hackers are the good guys of the hacker world. These people use the same technique used by the black hat hackers. They also hack the system, but they can only hack the system that they have permission to hack in order to test the security of the system. They focus on security and protecting IT system. White hat hacking is legal.Gray Hat Hacker
Gray hat Hackers are Hybrid between Black hat Hackers and White hat hackers. They can hack any system even if they don't have permission to test the security of the system but they will never steal money or damage the system. In most cases, they tell the administrator of that system. But they are also illegal because they test the security of the system that they do not have permission to test. Grey hat hacking is sometimes acted legally and sometimes not.Miscellaneous Hackers
Apart from the above well-known classes of hackers, we have the following categories of OMŃNHUV NMVHG RQ ROMP POH\ OMŃN MQG ORR POH\ GR LP íRed Hat Hackers
Red hat hackers are again a blend of both black hat and white hat hackers. They are usually on the level of hacking government agencies, top-secret information hubs, and generally anything that falls under the category of sensitive information.Blue Hat Hackers
A blue hat hacker is someone outside computer security consulting firms who is used to bug-test a system prior to its launch. They look for loopholes that can be exploited and try to close these gaps. Microsoft also uses the term BlueHat to represent a series of security briefing events.Elite Hackers
This is a social status among hackers, which is used to describe the most skilled. Newly discovered exploits will circulate among these hackers.Script Kiddie
A script kiddie is a non-expert who breaks into computer systems by using pre-packaged automated tools written by others, usually with little understanding of the underlying concept, hence the term Kiddie.Neophyte
A neophyte, "n00b", or "newbie" or "Green Hat Hacker" is someone who is new to hacking or phreaking and has almost no knowledge or experience of the workings of technology and hacking.Hacktivist
A hacktivist is a hacker who utilizes technology to announce a social, ideological, religious, or political message. In general, most hacktivism involves website defacement or denialof- service attacks.Phreaker
Phreaker is a telecom network hacker who hacks a telephone system illegally to make calls without paying for them.State/Nation Sponsored Hackers
State or Nation sponsored hackers are those who are appointed by the government to provide them cybersecurity and to gain confidential information from other countries to stay at the top or to avoid any kind of danger to the country. They are highly paid government workers.Malicious Insider or Whistleblower
A malicious insider or a whistleblower could be an employee of a company or a government agency with a grudge or a strategic employee who becomes aware of any illegal activities happening within the organization and can blackmail the organization for his/her personal gain.Differences Between the Law and Ethics:
It is impossible or impractical to develop laws to describe and enforce all forms of behavior acceptable
to society. Instead, society relies on ethics or morals to prescribe generally accepted standards of proper
behavior.Contrast of Law vs. Ethics.
Law Ethics
Described by formal, written documents Described by unwritten principles Interpreted by courts Interpreted by each individualEstablished by legislatures representing all
people Presented by philosophers, religions, professional groupsApplicable to everyone Personal choice
Priority determined by courts if two laws
conflictPriority determined by an individual if two
principles conflict Court is final arbiter of "right" No external arbiter Enforceable by police and courts Limited enforcementAssignment:
Describe the following terms: Digital SignatureElectronic Signature
Session hijacking
Scanning & Spoofing
Cyber laws to be covered as per IT Act 2008:
ͻ Section 43 Penalty and Compensation for damage to computer, computer system, etc. ͻ Section 65 Tampering with Computer Source Documents.ͻ Section 66 A Punishment for sending offensiǀe messages through communication service etc.
ͻ Section 66 B Punishments for dishonestly receiǀing stolen computer resource or communication device. ͻ Section 66C Punishment for identity theft. ͻ Section 66D Punishment for cheating by personation by using computer resource. ͻ Section 66E Punishment for ǀiolation of priǀacy. ͻ Section 66F Punishment for cyber terrorism.ͻ Section 67 Punishment for publishing or transmitting obscene material in electronic form.
ͻ Section 67A Punishment for publishing or transmitting of material containing sexually explicit
act, etc. in electronic form [Section 67B] Punishment for publishing or transmitting of material depicting children in sexually explicit act, etc. in electronic form. ͻ Section 72 Breach of confidentiality and priǀacy.quotesdbs_dbs10.pdfusesText_16[PDF] learn by doing: google docs unit 6
[PDF] learn c programming for beginners pdf
[PDF] learn c sharp tutorialspoint
[PDF] learn cbse class 9 math
[PDF] learn cisco network administration in a month of lunches
[PDF] learn cisco networking basics
[PDF] learn cisco networking pdf
[PDF] learn clojure
[PDF] learn cobol in 21 days pdf
[PDF] learn coding from scratch pdf
[PDF] learn data cleaning in r
[PDF] learn english grammar in tamil
[PDF] learn english grammar in tamil language
[PDF] learn english grammar step by step pdf
