|
HTTP Requests and Header Settings
The server performs an HTTP POST in response to a case-sensitive URL of the Cisco Unified IP Phones populate the Accept-Language HTTP request header in ... |
|
Add a title
HTTP request and response header names should be considered case insensitive as per HTTP rely on case sensitive matching of headers in your code. |
|
Add a title
HTTP request and response header names should be considered case insensitive as per HTTP rely on case sensitive matching of headers in your code. |
|
SMP Software Architecture Document Service Metadata Publisher
1 oct. 2018 Identifier's case sensitivity . ... ServiceGroup-Owner HTTP header - Specifying Owner User ............................................... |
|
Available mechanisms to modify HTTP data within IBM ® Security
5 sept. 2019 Matching on resource URIs is case sensitive. To have ... Controls the addition of HTTP headers into the request that is passed to junctioned. |
|
HTTP Requests and Header Settings
The server performs an HTTP POST in response to a case-sensitive URL of Cisco Unified IP Phones populate the Accept-Language HTTP request header in. |
|
BIG-IP Local Traffic Management: Getting Started with Policies
27 déc. 2017 Use case sensitive string comparison. HTTP Header. • Skip this condition if it is missing from the request. • Use case sensitive string ... |
|
Pulse Secure Services Director v19.1 Splunk Deployment Guide
20 mai 2019 Setting Up Case-Insensitive Searches for HTTP Headers . ... Log records are exported with HTTP POST requests and can also be sent. |
|
Service Provider Device Configuration Version 2.0 28 February 2015
28 févr. 2015 Case-Sensitive. Table 1: HTTP configuration: HTTPS request GET parameters. NOTE: a service specific document could define additional ... |
|
EIDR 2.6 API PROXY
8 déc. 2014 The EIDR API Proxy uses the following HTTP request headers for all ... NOTE: The “Eidr” authentication scheme token is case-insensitive. |
|
Make response headers case insensitive · Issue 㢲 - GitHub
30 jan 2022 · I am currently using Starlette (Python library) to send the PDF using Range requests but PDF js does not correctly detect when the headers are |
|
HTTP Requests and Header Settings - Cisco
Chapter 5 HTTP Requests and Header Settings HTTP Header Settings The form that is posted should have a case-sensitive form field name called “XML” that |
|
Are HTTP headers (Content-Type &c) case-sensitive? [duplicate]
Looks like the MIME type in a Content-type header value is case-insensitive so application/PDF and application/ pdf are equivalent |
|
Handling the Client Request: HTTP Request Headers - WikiEducator
Reading Request Headers (Methods in HttpServletRequest) • General – getHeader (header name is not case sensitive) – getHeaders – getHeaderNames |
|
Setting Up Case-Insensitive Searches for HTTP Headers
The built-in header filters always search using title case For example HTTP Request Header User-Agent If you require case insensitivity for other data |
|
HTTP Request Headers attributes are being Case-Sensitive after
25 avr 2022 · The application functionality of accessing the HTTP Request Headers attributes is behaving differently when applying policies For Example |
|
Request Header - Akamai TechDocs
The request header match is often used to match against a particular Case-sensitive value: If you select this option the value in the incoming request |
|
List of HTTP header fields - Wikipedia
HTTP header fields are a list of strings sent and received by both the client program and server on every HTTP request and response |
|
Web Service Enrichment Policy Match Criteria Imperva
This parameter is case sensitive To set user-defined request headers use the Headers match criteria HTTP Request Cookies |
|
HTTP class pattern string filters are case-sensitive - MyF5
21 août 2014 · The HTTP class will now send all requests containing a case-insensitive host header of www askf5 com to the defined resource |
Are HTTP request headers case sensitive?
All HTTP header keys are converted to lowercase in both directions (since HTTP header keys are defined to be case-insensitive). You should use lowercase in all of your mapping and classification rules.Are browser headers case sensitive?
HTTP headers let the client and the server pass additional information with an HTTP request or response. An HTTP header consists of its case-insensitive name followed by a colon ( : ), then by its value.Are curl headers case sensitive?
HTTP headers are case insensitive so the case must not matter to anyone speaking HTTP proper- The only valid value for this header is true (case-sensitive).
|
Cross-Origin Resource Sharing, W3C Working Draft 3 April 2012
1 sept 2012 · and also limit unsafe HTTP requests that can be automatically Allow- Credentials header with the case-sensitive string "true" as value |
|
HTTP Requests and Header Settings - Cisco
The Cisco Unified IP Phone HTTP client performs an HTTP GET for a specified The server performs an HTTP POST in response to a case-sensitive URL of |
|
Available mechanisms to modify HTTP data within IBM ® Security
5 sept 2019 · Matching on resource URIs is case sensitive To have Controls the addition of HTTP headers into the request that is passed to junctioned |
|
Handling the Client Request: HTTP Request Headers
Reading Request Headers (Methods in HttpServletRequest) • General – getHeader (header name is not case sensitive) – getHeaders – getHeaderNames |
|
User Guide - Illinoisgov
11 avr 2016 · "NewAck" and "LastAck", neither of which is case sensitive extended HTTP request header X-eFileRequestCode, and the Content-Type |
|
Documentation
1 fév 2021 · testing functions to assert that HTTP requests were---or were not---made Test that an HTTP request is made with a header Description logical: if FALSE, the pattern matching is case sensitive and if TRUE, case is ignored |
|
API Gateway Developer Guide
3 mar 2021 · avoid a large error in the value of the X-Sdk-Date request header The backend of this API is a fake HTTP service, which returns response code 200 and message The names of header parameters are not case-sensitive |
|
Reading Request Headers from Servlets - Higher Education Pearson
HTTP 1 1 request headers, response headers, and status codes only a single value Parameter names are case sensitive, so, for example, request get- |
|
Hypertext Transfer Protocol -- HTTP/11 - RFC Editor
1 jui 1999 · methods, error codes and headers [47] Request Header Fields HTTP-date is case sensitive and MUST NOT include additional LWS |
|
A Beginners Guide to Consuming RESTful Web Services in SAS®
technology like HTTP and machine-readable file formats like XML and JSON Methods are case sensitive and should always be upper cased Method Type of Header Headers are used to send additional information to with a request |
|
[PDF] HTTP Requests and Header Settings - Cisco
The server performs an HTTP POST in response to a case sensitive URL of the phone with this format xxxx CGI Execute, where xxxx represents the IP |
|
[PDF] RFC 2616 - Hypertext Transfer Protocol -- HTTP/11
Jun 1, 1999 · methods, error codes and headers [47] Request Header Fields HTTP date is case sensitive and MUST NOT include additional LWS |
|
[PDF] Header Manipulation Rules Resource Guide - Oracle Help Center
Jan 1, 2012 · response headers or the Request URI in a request, and change the status code or reason phrase By default, regular expressions are case sensitive, so A and a are u= csuclacuk staff MHandley sdp03ps |
|
[PDF] Available mechanisms to modify HTTP data within IBM ® Security
Sep 5, 2019 · Matching on resource URIs is case sensitive To have all of the elements of the HTTP Request object to be used in the response |
|
[PDF] The TAXII HTTP Protocol Binding Specification
Nov 16, 2012 · the network This document describes how to use HTTP to convey TAXII messages 52 Request Headers This field is case sensitive |
|
[PDF] Handling the Client Request: HTTP Request Headers
Reading Request Headers (Methods in HttpServletRequest) • General – getHeader (header name is not case sensitive) – getHeaders – getHeaderNames |
|
[PDF] Brocade Virtual Traffic Manager - Pulse Secure
Jul 3, 2017 · requestpost( url, POST data, [ headers ], [ timeout ] ) TrafficScript function names are not case sensitive |
- HTTP request flowWhat is an HTTP request
- HTTP GET request example
- HTTP GET request-response
- HTTP request response model
- HTTP request components
- Raw HTTP request

PDF) Analysis of the Adoption of Security Headers in HTTP
Source:https://i1.rgstatic.net/publication/340236424_HTTP_SECURITY_HEADERS/links/5e859f0b299bf1307970f1a4/largepreview.png
PDF) HTTP SECURITY HEADERS
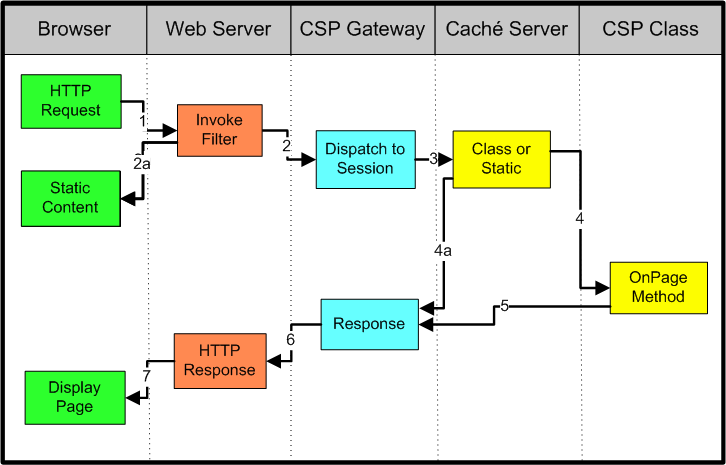
Source:https://docs.intersystems.com/latest/csp/docbook/images/gcsp_httprequest.png

HTTP Requests in CSP - Using Caché Server Pages (CSP) - Caché
Source:https://aws1.discourse-cdn.com/uipath/original/3X/f/3/f3c30c768b502ef6b1a6b7a19ffe298eaeb7a9d9.png

Save pdf using HTTP request - Studio - UiPath Community Forum
Source:https://user-images.githubusercontent.com/31785433/78269409-d6f8b380-7509-11ea-86c5-32720fb68640.png

GitHub - filipi86/MalwareAnalysis-in-PDF: Malicious PDF files
Source:https://media.springernature.com/original/springer-static/image/chp%3A10.1007%2F978-3-030-63089-8_29/MediaObjects/488418_1_En_29_Fig1_HTML.png

Detection of Malicious HTTP Requests Using Header and URL Features
Source:https://aws1.discourse-cdn.com/uipath/optimized/3X/7/2/72234dcb793ea9f0fe86f338973172ae34e7f3b4_2_545x500.jpeg
http response header injection exploit
[PDF] Vulnerability Report - 400 Bad Request
- HTTP response splitting exploit
- HTTP response splitting vulnerability fix java
- HTTP header injection
- HTTP header injection prevention Java
- [PDF] Vulnerability Report - 400 Bad Requestdl.packetstormsecurity.net › 1704-exploits › codeigniter-inject
- Mar 8
- 2017 · Particularly
- an HTTP Response Header Injection has been found in the current version of the framework. Several attacks with different impacts ...Detecting Drive-by-Download Attacks based on HTTP Context-Typesjournals.sfu.ca › apan › index.php › apan › article › download › pdf_120
- Index Terms— Network Security
- Malware
- HTTP Header
- ... (3) Attack. (4) download. Injection page. Redirector page. Exploit page ... HTTP response header.Related searchesHttp response splitting payload github
- Header manipulation attack
- HTTP response splitting tutorial
- HTTP Response Splitting HackerOne
- Security HTTP response splitting vulnerability
- HTTP response splitting bwapp
- Unvalidated data in an HTTP response header
- HTTP response Splitting PortSwigger
http response splitting bwapp
[PDF] Commix: Automating Evaluation and Exploitation of - ReCRED
- HTTP response splitting prevention
- HTTP response splitting (root me)
- HTTP response splitting tutorial
- Http response splitting payload github
- [PDF] Zranitelná webová aplikace jako didaktická pomůckadspace.cvut.cz › handle › F8-DP-2019-Dvoracek-Tomas-thesis
- Jan 8
- 2019 · WebGoat [3]
- DVWA [4] a bWAPP [5]. ... URL: /bWAPP/smgmt_cookies_.php ... Zranitelnost: HTTP Response splitting.[PDF] OWASP Methodologies to know and to test ... - ISWATlabwww.iswatlab.eu › wp-content › uploads › 2015/09 › OWASP_Meth...
- Testing for HTTP Splitting/Smuggling (OTG-INPVAL-016). ▻ Testing for ... ▻ Configure token position in HTTP response. ▻Start live ... Web Application: bWapp.[PDF] alert("XSS") - XSSerxsser.03c8.net › xsser › XSS_for_fun_and_profit_SCG09_(spanish)
- También es conocido como HTTP Response Splitting. Un atacante puede cambiar el contenido HTML completo de una página web a través de la manipulación ...[PDF] Commix: Automating Evaluation and Exploitation of ... - ReCREDwww.recred.eu › sites › default › files › commix-automating_evaluati...
- Feb 5
- 2018 · results
- simply
- by reading the response of the web application. In the rest of this ... into the "addr" parameter of the HTTP GET request the following commands: ... InputFormat none (Get - Content % temp %\ VVKBSV . txt ). split (" ") ... Extremely buggy web app (bWAPP) [31] includes two web applications.Related searchesHTTP response header injection exploit
- HTTP response Splitting PortSwigger
- What is HTTP response splitting attack
- HTTP Response Splitting HackerOne
- Response sendredirect HTTP response Splitting
- PHP HTTP response splitting
- Http response splitting wiki
- Security HTTP response splitting vulnerability
http response splitting payload
[PDF] Header injection tutorial - Real Solutions
- Http response splitting payload github
- HTTP response splitting prevention
- HTTP response splitting tutorial
- HTTP Response Splitting HackerOne
- [PDF] owasp ruby on rails security guide - OWASP Foundationwww.owasp.org › images › Rails_Security_2
- CSS Injection. 3. Textile Injection. 3. Ajax Injection. 3. RJS Injection. 3. Command Line Injection. 3. Header Injection. 3. Secure MySQL. 3. Access rights. 3. Users.[PDF] exploiting and automated detection of vulnerabilities in web ...www.zemris.fer.hr › ~sgros › diploma_thesis › suhina_vanja_seminar
- victim to follow the link to the bank's web site with the malicious payload in the parameter. The ... vulnerability to perform HTTP Response splitting attack [16.].[PDF] Header injection tutorial - Real Solutionsrealsolutions.services › uploads
- HTTP header injection is a vulnerability that occurs when hypertext transfer ... may beif the attacker is an attackerto enter a payload via HTTP header injection.Related searchesHTTP response header injection exploit
- HTTP response Splitting PortSwigger
- Response sendredirect HTTP response Splitting
- Http response splitting wiki
- Response splitting mitigation
- How to split response in java
- Spring HTTP Response Splitting
- PHP HTTP response splitting
http response splitting payload github
[PDF] SSRF bible Cheatsheet - Zenk - Security
- SSRF cheat sheet
- SSRF cheat sheet GitHub
- CRLF injection
- SSRF payloads
- [PDF] Automatic and Context-Aware Cross-Site Scripting Filter Evasion p g ...www.dis.uniroma1.it › biblioteca › RePEc › aeg › report
- than in the reflected XSS
- since the payload is displayed to any visitor. ... another severe vulnerability
- called HTTP response splitting
- 5 which is associated with many ... 9Symphony CMS
- xssfilter
- https://github.com/symphonycms/xssfilter. 32 ...[PDF] Practical Web Cache Poisoning: Redefining ... - PortSwiggerportswigger.net › papers › web-cache-poisoning
- poisoning caches - you can also use HTTP Response Splitting and Request ... Exploiting an unkeyed input isn't always as easy as pasting an XSS payload. ... wordlist by downloading and scouring the top 20
- 000 PHP projects on GitHub for.[PDF] Uplink Documentationuplink.readthedocs.io › downloads › pdf
- Mar 13
- 2019 · Uplink turns your HTTP API into a Python class. ... so the response we get back from GitHub is wrapped inside a requests. ... The Body annotation declares the JSON payload: ... owner
- repo_name = data["full_name"].split("/").[PDF] SSRF bible. Cheatsheet - Zenk - Securityrepo.zenk-security.com › ...
- HTTP response encapsulation into XML formatted response. 2 ... PHP (require dlopen
- but not exec):аhttps://github.com/dhotson/fdopenphp ... Basically restrictions which you may find in SSRF exploitation can be split into two groups:.Related searchesCRLF injection payloads
- CRLF injection Tutorial
- SSRF bible
- SSRF attack cheat sheet
- Ssrf bypass orange
- Xip io SSRF
- SSRF filter bypass
- SSRF exploit