 Boost Technical Design Document
Boost Technical Design Document
19-May-2022 This has a website make which comes with ready made website templates which are ideal for business owners who want a well-designed and fully ...
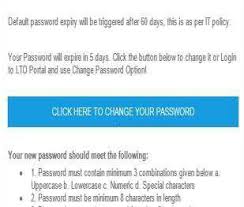 Technical Design document (Template)
Technical Design document (Template)
policy. • User Account locking after five unsuccessful attempts. o. Disabling user account in case of non-usage for a long duration (20 Months).
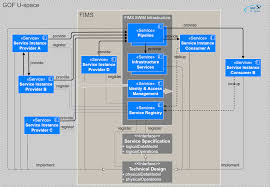 SESAR 2020 GOF USPACE Summary FIMS Design and Architecture
SESAR 2020 GOF USPACE Summary FIMS Design and Architecture
The technical aspects are described in a Technical Design using a standardized document template. At a minimum the logical contract defined in the Service
 Technical Design Document
Technical Design Document
23-Feb-2018 #1 This document explains technical characteristics of the web-based tool that is ... #1 Developer proposes the template for page design. #2 The ...
 System Design Document Template
System Design Document Template
▫ Application Design and Database Design. ▫ Application Programming Interfaces / Systems Integration. ▫ Application Technical Specifications Document. The
 DOC-CN-10567-1.0 SNC Policy Document Template
DOC-CN-10567-1.0 SNC Policy Document Template
Integration Design Document Template. Page: 2 of 13. Table of Contents. 1 This document is intended to enable ServiceNow Certification Engineers and Technical ...
 Technical design document template
Technical design document template
Technical design document template agile. Technical documentation refers to the documents that describe the features and functionalities of a product.
 System Design Document Template
System Design Document Template
30-Sept-2017 Figure 11: Example of a database design ... • Review requirements specifications and technical design documents to provide timely and.
 NASA Systems Engineering Handbook
NASA Systems Engineering Handbook
Technical Processes and the SE Engine . . . . . . . . . . . 5. 2.2 An ... design. HITL testing should also be approached as a debugging exercise where ...
 Technical Design Document TDD-002 – Business Central
Technical Design Document TDD-002 – Business Central
03-Oct-2022 Activate the type of master data required as a global template for the company. 4.3.2 JNP Global Company Release Setup. Include the type of ...
 System Design Document Template
System Design Document Template
Sep 30 2017 1.1 Purpose of the System Design Document (SDD) ... Review requirements
 Technical Design Document
Technical Design Document
Technical Design Document. Section 1 – List of Features Captured from GDD. 1.1 List of Features Based on the Game Design Document: • Third person.
 It Technical Design Document Templates
It Technical Design Document Templates
Word documents and not being able to see specifically when and where a certain change was made. How it may be designed to design documents and templates
 FUNCTIONAL and TECHNICAL REQUIREMENTS DOCUMENT
FUNCTIONAL and TECHNICAL REQUIREMENTS DOCUMENT
This document explains the high-level technical and functional o Will provide the manpower to design and develop the web-based application. Given other.
 MITRE Technical Document Template 2020
MITRE Technical Document Template 2020
This document contains comments and feedback from subject matter experts in for usability testing using Section 508 design guidelines does not stand.
 Design Document Template - Chapters
Design Document Template - Chapters
Apr 13 2004 List any documents that are related to the document
 Software Design Document Testing
Software Design Document Testing
https://arxiv.org/pdf/1005.0169
 DOC-CN-10567-1.0 SNC Policy Document Template
DOC-CN-10567-1.0 SNC Policy Document Template
Integration Design Document Template. Page: 2 of 13 This document is intended to enable ServiceNow Certification Engineers and Technical Support.
 Rain Gardens for RainScapes Technical Design Manual
Rain Gardens for RainScapes Technical Design Manual
Design planting layout or use a Rain Garden Template that is sized for your Take photos to document all steps of the installation process to assist in ...
 Functional Technical Specifications Template
Functional Technical Specifications Template
May 25 2004 C:Documents and Settingspxs23Desktopworkflow-epro.doc ... We used the workflow builder to design custom workflow rules
What is technical documentation?
Technical documentation refers to the documents that describe the features and functionalities of a product. It is most commonly created in the software development industry by development and product teams and it can fulfill the support needs of different stakeholders across an organization. They explain products.
What are the different types of technical documents?
A wide range of documents can be referred to as technical documents. Broadly speaking, they can be separated into two categories: product documentation and process documentation. Product documentation, sometimes referred to as user documentation, explains what a product is and how to use it.
What is a technical design document (TDD)?
A Technical Design Document (TDD) is written by the development team and describes the minute detail of either the entire design or specific parts of it, such as: The signature of an interface, including all data types/structures required (input data types, output data types, exceptions)
How to create a technical documentation sample plan?
Like any other written project, the easiest way to create the technical documentation sample plan is to follow a few steps rather than try to dive right in and start writing. The easiest way to make sure is that the thing you’re creating is useful, valuable, and clear.
UNCLASSIFIED
UNCLASSIFIED
MITRE Response to
Pre-Draft Call for
Comments: NIST
SP 800-63-4
The views, opinions and/or findings contained in this report are those of The MITRE Corporation and should not be construed as an official government position, policy, or decision, unless designated by other documentation.For Release
to All NIST. This document was prepared for authorized distribution only. It has not been approved for public release. ©2020 The MITRE Corporation. All rights reserved.Author:
Christopher J. Brown
A ugust 2020 Document No:MP200648
UNCLASSIFIED
UNCLASSIFIED
iiTable of Contents
Introduction
........................................................... 1 Accessibility ........................................................................ ........................................................... 1Artificial Intelligence/Machine Learning ................................................................................... 2
Authentication at Scale ........................................................................ ......................................... 2 Decentralized Identity ........................................................................ .......................................... 3 Privacy ........................................................................ ................................................................... 4800-63A ........................................................................
.................................................................. 4 ................................................................... 5 Memorized Secrets ........................................................................ ............................................. 5 Out-of-band Device ........................................................................ ............................................ 6Single-Factor One-Time Password Device ................................................................................. 6
800-63C ........................................................................
.................................................................. 6 Federation Relationships ........................................................................ ..................................... 7 References ........................................................................ .............................................................. 0 Abbreviations and Acronyms ........................................................................ .............................. 1UNCLASSIFIED
UNCLASSIFIED
iiiContributors
This document contains comments and feedback from subject matter experts across MITRE, including:Lorrayne Auld
Ronna ten Brink
Chris Buchanan
Russ Reopell
Rebecca Scollan
Jim Thomson
Mary Yang
UNCLASSIFIED
UNCLASSIFIED
1Introduction
MITRE's mission is to solve problems for a safer world. We work across the whole of government, through the federally funded research and development centers (FFRDCs) we manage and numerous public-private partnerships, to tackle difficult problems that challenge the safety, stability, and well-being of our nation. Our unique role and perspective allow us to provide innovative, practical solutions for some of our nation's most critical challenges in defense and intelligence, aviation, civil systems, financial systems, homeland security, the judiciary, healthcare, and cybersecurity.MITRE has performed independent research, such as
developing a methodology, detailed processes, and practice statement templates to proof digital identities at high assurance levels to help advance the state of the possible in the Identity, Credential, and Access Management (ICAM) domain. We also have experience assisting multiple federal agencies as they address prior and current ICAM requirements, and through our support for our sponsors, we have gained insight into private sector adoption of identity standards and technologies' capabilities to meet ICAM requirements. We thus welcome this opportunity to draw on our technical knowledge and broad operational experience to respond to National Institute of Standards and Technology's (NIST's) pre-draft call for comments for the next revision of the Digital Identity Guidelines, NISTSpecial Publication 800-63-3.
Since publication in 2017, the
Digital Identity Guidelines have had significant adoption within all branches of theU.S. government and modest adoption (voluntarily)
within private organizations. MITRE has also observed commercial identity service providers use their alignment with 800-63-3 as a competitive advantage in their marketing strategy. However, we believe opportunity exists for further adoption of theDigital
Identity Guidelines across critical
sectors of the U.S. economy to increase the security of online transactions that continue to be vulnerable.Modest changes to the
Digital Identity Guidelines that continue and expand on the multidisciplinary and collaborative approach - to include the Privacy Framework, UserExperience (UX), Cybersecurity Framework 1.1
, accessibility, and biometrics - will facilitate the continued adoption of the guidance and contribute to securing the nation's critical resources. The upcoming sections of this document highlight cross-cutting topic areas applicable to the development of 800-63-4. The final three sections discuss specific areas that address each volume of the current guidance.Accessibility
Throughout 800-63-3 it is stated, "Accessibility differs from usability and is out of scope for this document. Section 508 was enacted to eliminate barriers in information technology and require federal agencies to make their elec tronic and information technology public content accessible to people with disabilities. Refer to Section 508 law and standards for accessibility guidance." MI TRE asserts the line between accessibility and usability need not be so stark; we do not recommend completely striking accessibility out of scope.Because
Section 508 provides
guidance on achieving at least minimum acceptable accessibility, in these documents, consider including considerations on usability for people with disabilities, which goes beyond basic accessibility and has much in common with existing usability considerations.UNCLASSIFIED
UNCLASSIFIED
2 Often, designing with "edge case" users in mind, like users with disabilities, creates innovative solutions that are more usable for everyone , including users without disabilities. For example, the Usability Considerations in 800-63B include suggestions to offer alternate authentication options, to write for a low literacy level, and to use high-contrast and 12+ size fonts (800-63B, Section 10.1). These suggestions are also inclusive of people with a variety of disabilities, people with cognitive disabilities, and people with color deficiency or vision loss, respectively. Additionally, Section 508 is important for accessibility, but it does no t necessarily correspond to a usable, accessible experience for all people. New or novel interactions might not be covered in508, and regardless,
we recommend testing with people with disabilities. Just as usability heuristics do not stand in for usability testing, using Section 508 design guidelines does not stand in for testing with actual users with disabilities. MITRE also recommends suggesting usability testing with targeted populations, especially when using interactions that may be new to some users. For example, interactions that include camera positioning on a mobile phone could pass 508 standards but not be accessible to blind or low- vision users.Artificial Intelligence/Machine Learning
Commercial cloud identity service providers have begun advertising artificial intelligence (AI) or machine learning (ML) capabilities as part of their solutions and to enhance the security of authentication transactions. MITRE recommends speaking to these capabilities in the next version of 800-63, as a supplemental technique for credential service providers (CSPs) to detect attacks, or to otherwise enhance an authentication transaction. We also recommend communicating the risk of utilizing AI capabilities: vulnerabilities can be created from adversarial AI/ML, and services that use AI/ML methods for authentication and readers of 800-63 should be aware of those vulnerabilities.
Authentication at Scale
As more transactions and engagements move online, being able to authenticate large groups (e.g., millions of diverse individuals) quickly with a measurable or high-level of assurance (based on the transaction's risk) will only become more important. The current COVID-19 pandemic highlights the need and urgency of this issue, though "authentication at scale" is not a new concern. Google identified the issue and coined this phrase back in 2013, documenting their perspective in IEEE Security & Privacy [1] Strong authentication at scale is an issue for both the public and private sectors. Numerous federal agencies support citizen and non-citizen online transactions that may consist of accessing or transmitting personally identifiable and sensitive information. With COVID-19, this list of agencies is only growing; prior to the pandemic, many federal agencies were pushing to move in- person or paper-based processes and transactions online to support digital modernization efforts and improve efficiencies. With the pandemic, these efforts have only accelerated. Private sector organizations, such as banks, have adopted some technologies that enable strong authentication at scale, but wide-scale adoption across diverse communities continues to lag. While authentication technologies have advanced since 2013, secure implementations to support authentication at scale based on standards remain, at best, ambiguous. Identiverse 2020 hosted a panel session [2] on this topic, and the discussion illustrated the lack of clarity surrounding it. AUNCLASSIFIED
UNCLASSIFIED
3 clearer definition of "authentication at scale," general use cases, and guidance on how organizations can address these concerns should be considered as additions to a revision of 800- 63.Decentralized Identity
Self-Sovereign or Decentralized Identity (DID) is the next evolutionary step in creating and managing identities on the internet from current stove-piped centralized identity and federated models. The ability to record, track, and manage identity on a blockchain [3] has the potential to vastly improve the efficiency and minimize the cost of identity management across all U.S. sectors; an immutable, trusted source of identity will make it difficult to steal, hack, modify, or otherwise damage reputation, or compromise identity to steal real assets or perpetrate fraud. Technology vendors and the private sector are beginning to investigate implementing DID more earne stly. Gartner"s recent report on 2020identity and access management (IAM) technologies and trends [4] indicated that DID is likely to see a strong surge in adoption. With its broadquotesdbs_dbs20.pdfusesText_26
[PDF] technical requirements examples
[PDF] technical solutions engineer epic interview
[PDF] technical solutions engineer epic job description
[PDF] technical solutions engineer epic review
[PDF] technical solutions engineer epic salary reddit
[PDF] technical solutions engineer epic systems
[PDF] technical solutions engineer team epic
[PDF] technical support fundamentals coursera quiz answers
[PDF] technical writing and communication skills pdf
[PDF] technical writing examples
[PDF] technique de vente et négociation ofppt pdf
[PDF] technique facile pour apprendre les tables de multiplication
[PDF] technique pour apprendre la table de 7
[PDF] techniques definition
