 Mobile Application Penetration Testing by Vijay Kumar Velu.pdf
Mobile Application Penetration Testing by Vijay Kumar Velu.pdf
book is to educate you about and demonstrate application security weaknesses on the client (device) side and configuration faults in Android and. iOS that ...
 Android Mobile Application Pentesting
Android Mobile Application Pentesting
٢٩/٠٤/٢٠١٨ First step into android mobile application penetration testing is to try reverse engineer the application because once u get the code u ...
 Penetration Testing Ten Popular Swedish Android Applications
Penetration Testing Ten Popular Swedish Android Applications
١٩/١٠/٢٠٢٢ OWASP's MSTG is manual which features procedures to test and verify compliance with requirements outlined in OWASP's Mobile Application Security ...
 Testing Guide
Testing Guide
BOOK TITLE. ALPHA: “Alpha Quality” book content ... It goes without saying that you can't build a secure application without performing security testing on it.
 Penetration Testing of Android-based Smartphones
Penetration Testing of Android-based Smartphones
Smartphone usage and adaptation are increasing day by day with a variety of applications. These applications can be very critical in nature such as mobile
 MOBILE APPLICATION PENETRATION TESTING
MOBILE APPLICATION PENETRATION TESTING
iOS apps can store files in various formats such as PDF
 OWASP API Top 10
OWASP API Top 10
٣١/٠٣/٢٠٢٣ • Conducted Black-box and Grey-box web application mobile application (iOS
 Penetration Testing Guidelines For the Financial Industry in Singapore
Penetration Testing Guidelines For the Financial Industry in Singapore
٣١/٠٧/٢٠١٥ The application penetration test should cover the critical risks identified in. OWASP Top Ten list for web application and mobile security as ...
 ETHICAL HACKING AND PENETRATION TESTING GUIDE
ETHICAL HACKING AND PENETRATION TESTING GUIDE
Mobile Application Penetration Test This book introduces the steps required to complete a penetration test or ethical hack.
 Instant Payment Network
Instant Payment Network
Penetration testing must be performed by an independent third- party service banking - mobile banking application). Submission of a three-year work plan ...
 Mobile Application Penetration Testing
Mobile Application Penetration Testing
He also gives talks and training on wireless pentesting and mobile app Did you know that Packt offers eBook versions of every book published with PDF.
 Android Mobile Application Pentesting
Android Mobile Application Pentesting
Apr 29 2018 Peace out yoo! Page 5. Android Mobile Application. Security Testing. Page 6 ...
 Mobile Application Security Testing
Mobile Application Security Testing
one-size-fits-all approach to mobile app security testing Developed a custom mobile app penetration testing set-up consisting of a device farm made up.
 2WTech
2WTech
iOS apps can store files in various formats such as PDF
 Testing Guide
Testing Guide
to guide to perform Web Application Penetration Testing. - Matteo. Meucci. OWASP thanks the many authors reviewers
 Penetration Testing - A hands-on introduction to Hacking.pdf
Penetration Testing - A hands-on introduction to Hacking.pdf
Nov 10 2015 The information in this book is distributed on an “As Is” basis
 Hands-On Mobile App Testing: A Guide for Mobile Testers and
Hands-On Mobile App Testing: A Guide for Mobile Testers and
Chapter 2: Introduction to Mobile Devices and Apps . . This book is a practical guide to mobile testing for anyone who works in the.
 XML Based Attacks
XML Based Attacks
Web/mobile application penetration tests. ? Internal network penetration tests. ? Curious about mobile and embedded devices. ? Bug bounty hunter.
 BUILDING A MOBILE APP PEN TESTING BLUEPRINT
BUILDING A MOBILE APP PEN TESTING BLUEPRINT
Books & Speaking. MOBILE SECURITY RESEARCH IS IN OUR DNA Pen tested thousands of mobile apps. Comprehensive experience and testing blueprint.
 ServiceNow Security Best Practice Guide
ServiceNow Security Best Practice Guide
Mobile application security . Vulnerability assessment and penetration testing . ... eBook. Certification. Description. Industry. Geography.
 [PDF] Mobile Application Penetration Testing
[PDF] Mobile Application Penetration Testing
Every effort has been made in the preparation of this book to ensure the accuracy of the information presented However the information contained in this book
 [PDF] Mobile Application Penetration Testing by Vijay Kumar Velu
[PDF] Mobile Application Penetration Testing by Vijay Kumar Velu
This book gives you the necessary skills to security test your mobile applications as a beginner developer or security practitioner You'll start by
 [PDF] Android Mobile Application Pentesting
[PDF] Android Mobile Application Pentesting
29 avr 2018 · Taken from learning pentesting for android device It is just a zip file First step into android mobile application penetration
 MOBILE APPLICATION PENETRATION TESTING BY VIJAY KUMAR
MOBILE APPLICATION PENETRATION TESTING BY VIJAY KUMAR
5 Explore real-world threat scenarios attacks on mobile applications and ways to counter them About This Book Gain insights into the current threat landscape
 Mobile Application Penetration Testing by Velu Vijay Kumar - Scribd
Mobile Application Penetration Testing by Velu Vijay Kumar - Scribd
11 mar 2016 · Explore real-world threat scenarios attacks on mobile applications and ways to counter them About This Book
 [PDF] Penetration Testing Ten Popular Swedish Android Applications - DiVA
[PDF] Penetration Testing Ten Popular Swedish Android Applications - DiVA
19 oct 2022 · OWASP's MSTG is manual which features procedures to test and verify compliance with requirements outlined in OWASP's Mobile Application Security
 [PDF] Penetration testing : a hands-on introduction to hacking - Zenk
[PDF] Penetration testing : a hands-on introduction to hacking - Zenk
10 nov 2015 · The information in this book is distributed on an “As Is” basis without warranty testing mobile hacking and exploit develop
 Mobile Application Penetration Testing - Packt
Mobile Application Penetration Testing - Packt
This book gives you the necessary skills to security test your mobile applications as a beginner developer or security practitioner
 Mobile Application Security Penetration Testing Based on OWASP
Mobile Application Security Penetration Testing Based on OWASP
28 mai 2020 · PDF Evolution of smartphones and smart devices affected one of the most used operating systems on smartphones and smart device is Android
 [PDF] Penetration Testing of Android-based Smartphones - CORE
[PDF] Penetration Testing of Android-based Smartphones - CORE
Research work on mobile operating systems began in 2000 and 2001 [7][8] which shows the security of memory protection permission-based file access control
How to test security testing in mobile application?
Use of SAST, DAST, and IAST techniques
Tools such as Klocwork and Checkmarx are useful for achieving SAST. Dynamic application security testing (DAST) focuses on a running app. DAST scan apps to check for any loopholes that may lead to security risks.What is mobile pentest vs web pentest?
Pentesting mobile apps requires additional permutation of testing strategies to think like hackers and test various platforms. On the other hand, web app pentesting is highly dependent on robust web browsers that involve testing real-time, simulated scenarios in various browsers on a remote network.What is the VAPT methodology of mobile application?
An android application is tested to identify any security flaws. This technique is known as Android VAPT. Decompiling, real-time analysis, and testing of the Android application under security conditions are all included.- DAST is a type of security testing that assesses the security of an application by testing it in its running state. This is in contrast to traditional penetration testing, which typically assesses the security of an application by testing it in a static state (in most cases).
Mobile Application
Penetration Testing
Explore real-world threat scenarios, attacks on mobile applications, and ways to counter themVijay Kumar Velu
BIRMINGHAM - MUMBAIwww.allitebooks.com
Mobile Application Penetration Testing
Copyright © 2016 Packt Publishing
All rights reserved. No part of this book may be reproduced, stored in a retrieval system, or transmitted in any form or by any means, without the prior wr itten permission of the publisher, except in the case of brief quotations embe dded in critical articles or reviews. Every effort has been made in the preparation of this book to ensure the accuracy of the information presented. However, the information contained in this book is sold without warranty, either express or implied. Neither the author, no r Packt Publishing, and its dealers and distributors will be held liable for any damages caused or alleged to be caused directly or indirectly by this book. Packt Publishing has endeavored to provide trademark information about a ll of the companies and products mentioned in this book by the appropriate use of capitals. However, Packt Publishing cannot guarantee the accuracy of this informat ion.First published: March 2016
Production reference: 1070316
Published by Packt Publishing Ltd.
Livery Place
35 Livery Street
Birmingham B3 2PB, UK.
ISBN 978-1-78588-337-8
www.allitebooks.comCredits
Author
Vijay Kumar Velu
Reviewers
Akash Mahajan
Swaroop Yermalkar
Commissioning Editor
Veena Pagare
Acquisition Editor
Aaron Lazar
Content Development Editor
Sachin Karnani
Technical Editor
Nirant Carvalho
Copy Editors
Stuti Srivastava
Madhusudan UchilProject Coordinator
Nikhil Nair
Proofreader
Indexer
Tejal Daruwale Soni
Graphics
Jason Monteiro
Production Coordinator
Melwyn Dsa
Cover Work
Melwyn Dsawww.allitebooks.com
About the Author
Vijay Kumar Velu is a passionate information security practitioner, speaker, and blogger, currently working as a cyber security technical manager at one of the Big4 consultancies based in India. He has more than 10 years of IT industry e xperience, is a licensed penetration tester, and has specialized in providing technica l solutions to a Forensics Investigator. He loves hands-on technological challenges. Vijay was invited to speak at the National Cyber Security Summit (NCSS) , Indian Cyber Conference (InCyCon), Open Cloud Conference, and Ethical Hacking Conference held in India, and he has also delivered multiple guest lectu res and training on the importance of information security at various business s chools inIndia. He also recently reviewed
Learning Android Forensics, Packt Publishing.
For the information security community, Vijay serves as the director of the Bangalore chapter of the Cloud Security Alliance (CSA) and chair member of the N ationalCyber Defence and Research Center (NCDRC).
I would like to dedicate this book to my mother and sister for believing in me and always encouraging me to do what I like with all my crazy ideas. Special thanks to my family, friends (Hackerz), core team (Rachel H Martis, Anil Dikshit, Karthik Belur Sridhar, Vikram Sridharan and Vishal Patel), and Lokesh Gowda for allowing me ample amount of time in shaping this book. A huge thanks to Darren Fuller, my mentor and friend, for providing his support and insights. Also to the excellent team at Packt Publishing for all the support that they provided throughout the journey of this book, specially Sachin and Nirant for their indubitable coordination.www.allitebooks.comAbout the Reviewers
Akash Mahajan is an accomplished security professional with over a decade's experience in providing specialist application and infrastructure consul ting services at the highest levels to companies, governments, and organizations aroun d the world. He is the author ofBurp Suite Essentials, Packt Publishing.
Akash is an extremely active participant in the international security c ommunity and a frequent conference speaker. He gives talks as himself, as the hea d of the standards for web application security, and as a co-founder of NULL, Ind ia's largest open security community. I want to thank you, Nikhil, for making sure that reviewing this book was a pleasurable experience.www.allitebooks.com Swaroop Yermalkar works as a healthcare security researcher at Philips Health Systems, India, where he is responsible for thread modeling; security re search; and the assessment of IoT devices, healthcare products, web applications, ne tworks, and Android and iOS applications. He is the author of the popular iOS securi ty book Learning iOS Penetration Testing, Packt Publishing and also one of the top mobile security researchers worldwide, working with Synack, Inc. He also gives talks and training on wireless pentesting and mobile app p entesting at various security conferences, such as GroundZero, c0c0n, 0x90, DEFCONLuc know, and GNUnify. He has been acknowledged by Microsoft, Amazon, eBay, Etsy, Dropbox, Ever note, Simple banking, iFixit, and many more for reporting high-severity securi ty issues in their mobile apps. He is an active member of NULL, an open security community in India, and is a contributor to the regular meetups and Humla sessions at the Pune chapte r.SWSE, CEH, and CHFI. He has written articles for
clubHACK magazine and also authored a book,An Ethical Guide to Wi-Fi Hacking and Security
He has organized many eminent programs and was the event head of Hackath on - a national-level hacking competition. He has also worked with Pune Cyber C ell, Maharashtra Police, in programs such as Cyber Safe Pune. He can be conta cted at on Twitter.www.allitebooks.com www.PacktPub.com eBooks, discount offers, and more Did you know that Packt offers eBook versions of every book published, w ith PDF and as a print book customer, you are entitled to a discount on the eBo ok copy.Get in touch with us at
for more details. At , you can also read a collection of free technical articles, sign up for a range of free newsletters and receive exclusive discounts and o ffers on Packt books and eBooks. book library. Here, you can search, access, and read Packt's entire libr ary of books.Why subscribe?
Fully searchable across every book published by PacktCopy and paste, print, and bookmark content
On demand and accessible via a web browserwww.allitebooks.com www.allitebooks.com [ i ]Table of Contents
Preface ix
Chapter 1: The Mobile
Application Security Landscape
1The smartphone market share 2
The android operating system
3The iPhone operating system (iOS)
3Different types of mobile applications
3Native apps
4Mobile web apps
4Hybrid apps
5Public
Android and iOS vulnerabilities
7Android vulnerabilities
9 iOS vulnerabilities 10The key challenges in mobile application security
1 1The impact of mobile application security
12 The need for mobile application penetration testing 13Current market reaction 13
The mobile application penetration testing methodology 14Discovery
14Analysis/assessment
15Exploitation
16Reporting
16The OWASP mobile security project
16 OWASP mobile top 10 risks
17 V ulnerable applications to practice 20Summary
20www.allitebooks.com
Table of Contents
[ ii ]Chapter 2: Snooping Around the Architecture 21
The importance of architecture 22
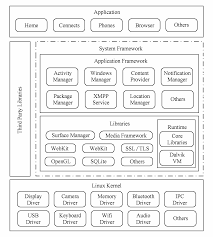
TheAndroid architecture
23The Linux kernel
24Confusion between Linux and the Linux kernel 24
Android runtime 25
The java virtual machine
26The Dalvik virtual machine
26Zygote 27
Core Java libraries 27
A RT 2 8Native libraries
28The application framework
29The applications layer
31Native Android or system apps 31
User-installed or custom apps
31The
Android software development kit
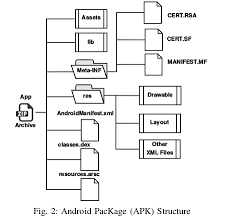
31Android application packages (APK)
32Android application components 36
Intent 36
Activity
36Services
38Broadcast receivers
40Content providers
41Android Debug Bridge 41
Application sandboxing
42Application signing
43Secure inter-process communication
43The Binder process 44
The Android permission model 45
TheAndroid application build process
46Android rooting
50iOS architecture 51
Cocoa T
ouch 53Media 53
Core services
54Core OS
55iOS SDK and Xcode 55
iOS application programming languages 56
Objective-C
56The Objective-C runtime 57
Swift 57
Table of Contents
[ iii ]Understanding application states 57
Apple's iOS security model
58Device-level security
59System-level security
59An introduction to the secure boot chain 59
System software authorization
60Secure Enclave
60Data-level security 60
Data-protection classes 61
Keychain data protection
62Changes in iOS 8 and 9 62
Network-level security
63Application-level security
63Application code signing 63
The iOS app sandbox 64
iOS isolation 64Process isolation
65Filesystem isolation
65ASLR 66
Stack protection (non-executable stack and heap)
66Hardware-level security
66iOS permissions 66
The iOS application structure
68Jailbreaking
69Why jailbreak a device?
70T ypes of jailbreaks 70
Untethered jailbreaks 70
T ethered jailbreaks 70Semi-tethered jailbreaks
70Jailbreaking tools at a glance 71
Inspecting a Mach-O binary
73Property lists
74Summary
75Chapter 3: Building a Test Environment 77
Mobile app penetration testing environment setup 77Android Studio and SDK
78The Android
SDK 81The
Android Debug Bridge
81Connecting to the device
82Getting access to the device
83Table of Contents
[ iv ]Installing an application to the device 84
Stopping the service
85V iewing the log information 85
Sideloading apps
86quotesdbs_dbs14.pdfusesText_20
[PDF] mobile application performance testing tools
[PDF] mobile application reference architecture
[PDF] mobile application security pdf
[PDF] mobile application security ppt
[PDF] mobile application security testing approach
[PDF] mobile application security testing checklist
[PDF] mobile application security testing pdf
[PDF] mobile application security testing ppt
[PDF] mobile application testing checklist xls
[PDF] mobile apps for language learning pdf
[PDF] mobile computing applications
[PDF] mobile computing architecture
[PDF] mobile computing framework
[PDF] mobile computing functions pdf
