 Mobile Application Penetration Testing by Vijay Kumar Velu.pdf
Mobile Application Penetration Testing by Vijay Kumar Velu.pdf
book is to educate you about and demonstrate application security weaknesses on the client (device) side and configuration faults in Android and. iOS that ...
 Android Mobile Application Pentesting
Android Mobile Application Pentesting
٢٩/٠٤/٢٠١٨ First step into android mobile application penetration testing is to try reverse engineer the application because once u get the code u ...
 Penetration Testing Ten Popular Swedish Android Applications
Penetration Testing Ten Popular Swedish Android Applications
١٩/١٠/٢٠٢٢ OWASP's MSTG is manual which features procedures to test and verify compliance with requirements outlined in OWASP's Mobile Application Security ...
 Testing Guide
Testing Guide
BOOK TITLE. ALPHA: “Alpha Quality” book content ... It goes without saying that you can't build a secure application without performing security testing on it.
 Penetration Testing of Android-based Smartphones
Penetration Testing of Android-based Smartphones
Smartphone usage and adaptation are increasing day by day with a variety of applications. These applications can be very critical in nature such as mobile
 MOBILE APPLICATION PENETRATION TESTING
MOBILE APPLICATION PENETRATION TESTING
iOS apps can store files in various formats such as PDF
 OWASP API Top 10
OWASP API Top 10
٣١/٠٣/٢٠٢٣ • Conducted Black-box and Grey-box web application mobile application (iOS
 Penetration Testing Guidelines For the Financial Industry in Singapore
Penetration Testing Guidelines For the Financial Industry in Singapore
٣١/٠٧/٢٠١٥ The application penetration test should cover the critical risks identified in. OWASP Top Ten list for web application and mobile security as ...
 ETHICAL HACKING AND PENETRATION TESTING GUIDE
ETHICAL HACKING AND PENETRATION TESTING GUIDE
Mobile Application Penetration Test This book introduces the steps required to complete a penetration test or ethical hack.
 Instant Payment Network
Instant Payment Network
Penetration testing must be performed by an independent third- party service banking - mobile banking application). Submission of a three-year work plan ...
 Mobile Application Penetration Testing
Mobile Application Penetration Testing
He also gives talks and training on wireless pentesting and mobile app Did you know that Packt offers eBook versions of every book published with PDF.
 Android Mobile Application Pentesting
Android Mobile Application Pentesting
Apr 29 2018 Peace out yoo! Page 5. Android Mobile Application. Security Testing. Page 6 ...
 Mobile Application Security Testing
Mobile Application Security Testing
one-size-fits-all approach to mobile app security testing Developed a custom mobile app penetration testing set-up consisting of a device farm made up.
 2WTech
2WTech
iOS apps can store files in various formats such as PDF
 Testing Guide
Testing Guide
to guide to perform Web Application Penetration Testing. - Matteo. Meucci. OWASP thanks the many authors reviewers
 Penetration Testing - A hands-on introduction to Hacking.pdf
Penetration Testing - A hands-on introduction to Hacking.pdf
Nov 10 2015 The information in this book is distributed on an “As Is” basis
 Hands-On Mobile App Testing: A Guide for Mobile Testers and
Hands-On Mobile App Testing: A Guide for Mobile Testers and
Chapter 2: Introduction to Mobile Devices and Apps . . This book is a practical guide to mobile testing for anyone who works in the.
 XML Based Attacks
XML Based Attacks
Web/mobile application penetration tests. ? Internal network penetration tests. ? Curious about mobile and embedded devices. ? Bug bounty hunter.
 BUILDING A MOBILE APP PEN TESTING BLUEPRINT
BUILDING A MOBILE APP PEN TESTING BLUEPRINT
Books & Speaking. MOBILE SECURITY RESEARCH IS IN OUR DNA Pen tested thousands of mobile apps. Comprehensive experience and testing blueprint.
 ServiceNow Security Best Practice Guide
ServiceNow Security Best Practice Guide
Mobile application security . Vulnerability assessment and penetration testing . ... eBook. Certification. Description. Industry. Geography.
 [PDF] Mobile Application Penetration Testing
[PDF] Mobile Application Penetration Testing
Every effort has been made in the preparation of this book to ensure the accuracy of the information presented However the information contained in this book
 [PDF] Mobile Application Penetration Testing by Vijay Kumar Velu
[PDF] Mobile Application Penetration Testing by Vijay Kumar Velu
This book gives you the necessary skills to security test your mobile applications as a beginner developer or security practitioner You'll start by
 [PDF] Android Mobile Application Pentesting
[PDF] Android Mobile Application Pentesting
29 avr 2018 · Taken from learning pentesting for android device It is just a zip file First step into android mobile application penetration
 MOBILE APPLICATION PENETRATION TESTING BY VIJAY KUMAR
MOBILE APPLICATION PENETRATION TESTING BY VIJAY KUMAR
5 Explore real-world threat scenarios attacks on mobile applications and ways to counter them About This Book Gain insights into the current threat landscape
 Mobile Application Penetration Testing by Velu Vijay Kumar - Scribd
Mobile Application Penetration Testing by Velu Vijay Kumar - Scribd
11 mar 2016 · Explore real-world threat scenarios attacks on mobile applications and ways to counter them About This Book
 [PDF] Penetration Testing Ten Popular Swedish Android Applications - DiVA
[PDF] Penetration Testing Ten Popular Swedish Android Applications - DiVA
19 oct 2022 · OWASP's MSTG is manual which features procedures to test and verify compliance with requirements outlined in OWASP's Mobile Application Security
 [PDF] Penetration testing : a hands-on introduction to hacking - Zenk
[PDF] Penetration testing : a hands-on introduction to hacking - Zenk
10 nov 2015 · The information in this book is distributed on an “As Is” basis without warranty testing mobile hacking and exploit develop
 Mobile Application Penetration Testing - Packt
Mobile Application Penetration Testing - Packt
This book gives you the necessary skills to security test your mobile applications as a beginner developer or security practitioner
 Mobile Application Security Penetration Testing Based on OWASP
Mobile Application Security Penetration Testing Based on OWASP
28 mai 2020 · PDF Evolution of smartphones and smart devices affected one of the most used operating systems on smartphones and smart device is Android
 [PDF] Penetration Testing of Android-based Smartphones - CORE
[PDF] Penetration Testing of Android-based Smartphones - CORE
Research work on mobile operating systems began in 2000 and 2001 [7][8] which shows the security of memory protection permission-based file access control
How to test security testing in mobile application?
Use of SAST, DAST, and IAST techniques
Tools such as Klocwork and Checkmarx are useful for achieving SAST. Dynamic application security testing (DAST) focuses on a running app. DAST scan apps to check for any loopholes that may lead to security risks.What is mobile pentest vs web pentest?
Pentesting mobile apps requires additional permutation of testing strategies to think like hackers and test various platforms. On the other hand, web app pentesting is highly dependent on robust web browsers that involve testing real-time, simulated scenarios in various browsers on a remote network.What is the VAPT methodology of mobile application?
An android application is tested to identify any security flaws. This technique is known as Android VAPT. Decompiling, real-time analysis, and testing of the Android application under security conditions are all included.- DAST is a type of security testing that assesses the security of an application by testing it in its running state. This is in contrast to traditional penetration testing, which typically assesses the security of an application by testing it in a static state (in most cases).
Android Mobile Application
Pentesting
Williams
wyohanes96@gmail.com OWASP29 April 2018
Who Am I ?
Who Am I
Noted to all audience:
Semua materi yang diberikan dalam pertemuan hanya
untuk tujuan pendidikan. Kerusakan yang terjadi pada suatu aplikasi sistem bukan merupakan tanggung jawab dari pengarangPeace out yoo!
Android Mobile Application
Security Testing
Source:
Source:
OWASP Mobile top 10 Vulnerability
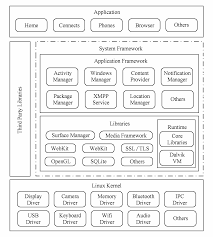
Linux KernelAndroid RuntimeNative LibrariesApplication frameworkApplicationTaken from learning pentesting for android device
Linux KernelAndroid RuntimeNative LibrariesApplication frameworkApplicationAndroid Application Package
It is just a zip ifile
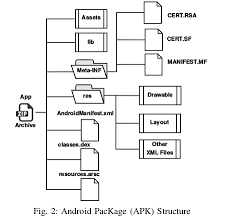
Android Application Package
Taken from: Android Security: A Survey of Issues, MalwarePenetration and Defenses
Android Application Package
Taken from: Android Security: A Survey of Issues, MalwarePenetration and Defenses
Android Application Package
Taken from: Android Security: A Survey of Issues, MalwarePenetration and Defenses
Taken from ifileinfo.com
OWASP Mobile top 10 Vulnerability
OWASP Mobile top 10 Vulnerability
First step into android mobile application penetration testing is to try reverse engineer the application because once u get the code u already do half of the worksWith APKTOOLS
With Dex2jar
With jdx-core
With jdx-core
Where to get Free apk other than play
store?Taken from APKpure.com
Improper Platform Usage
Improper Platform Usage
Improper Platform Usage
A Good Tools that every android
pentester must haveTaken from mac
afee blog. All right reserved to the authorTarget:
Improper Platform Usage
Improper Platform Usage
Improper Platform Usage
~# adb shell am start -n com.xllusion.quicknote/.EditNote -eandroid.intent.extra.SUBJECT dumbass -e android.intent.extra.TEXT dumbass Package name and the activity
Put the ifirst stringPut the second string
Improper Platform Usage
OWASP Mobile top 10 Vulnerability
Insecure Data Storage
Target:
Insecure Data Storage
Insecure Data Storage
Insecure Data Storage
Insecure Data Storage
Insecure Data Storage
OWASP Mobile top 10 Vulnerability
Insecure Communication
What do you need ?
Insecure Communication
Insecure Communication
Insecure Communication
Insecure Communication
Insecure Communication
Insecure Communication
Insecure Communication
Thank You
quotesdbs_dbs21.pdfusesText_27[PDF] mobile application performance testing tools
[PDF] mobile application reference architecture
[PDF] mobile application security pdf
[PDF] mobile application security ppt
[PDF] mobile application security testing approach
[PDF] mobile application security testing checklist
[PDF] mobile application security testing pdf
[PDF] mobile application security testing ppt
[PDF] mobile application testing checklist xls
[PDF] mobile apps for language learning pdf
[PDF] mobile computing applications
[PDF] mobile computing architecture
[PDF] mobile computing framework
[PDF] mobile computing functions pdf
