 Mobile Application Penetration Testing by Vijay Kumar Velu.pdf
Mobile Application Penetration Testing by Vijay Kumar Velu.pdf
book is to educate you about and demonstrate application security weaknesses on the client (device) side and configuration faults in Android and. iOS that ...
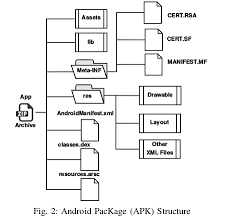 Android Mobile Application Pentesting
Android Mobile Application Pentesting
٢٩/٠٤/٢٠١٨ First step into android mobile application penetration testing is to try reverse engineer the application because once u get the code u ...
 Penetration Testing Ten Popular Swedish Android Applications
Penetration Testing Ten Popular Swedish Android Applications
١٩/١٠/٢٠٢٢ OWASP's MSTG is manual which features procedures to test and verify compliance with requirements outlined in OWASP's Mobile Application Security ...
 Testing Guide
Testing Guide
BOOK TITLE. ALPHA: “Alpha Quality” book content ... It goes without saying that you can't build a secure application without performing security testing on it.
 Penetration Testing of Android-based Smartphones
Penetration Testing of Android-based Smartphones
Smartphone usage and adaptation are increasing day by day with a variety of applications. These applications can be very critical in nature such as mobile
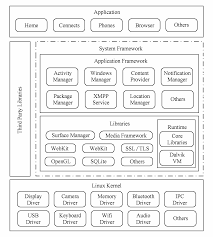
 MOBILE APPLICATION PENETRATION TESTING
MOBILE APPLICATION PENETRATION TESTING
iOS apps can store files in various formats such as PDF
 OWASP API Top 10
OWASP API Top 10
٣١/٠٣/٢٠٢٣ • Conducted Black-box and Grey-box web application mobile application (iOS
 Penetration Testing Guidelines For the Financial Industry in Singapore
Penetration Testing Guidelines For the Financial Industry in Singapore
٣١/٠٧/٢٠١٥ The application penetration test should cover the critical risks identified in. OWASP Top Ten list for web application and mobile security as ...
 ETHICAL HACKING AND PENETRATION TESTING GUIDE
ETHICAL HACKING AND PENETRATION TESTING GUIDE
Mobile Application Penetration Test This book introduces the steps required to complete a penetration test or ethical hack.
 Instant Payment Network
Instant Payment Network
Penetration testing must be performed by an independent third- party service banking - mobile banking application). Submission of a three-year work plan ...
 Mobile Application Penetration Testing
Mobile Application Penetration Testing
He also gives talks and training on wireless pentesting and mobile app Did you know that Packt offers eBook versions of every book published with PDF.
 Android Mobile Application Pentesting
Android Mobile Application Pentesting
Apr 29 2018 Peace out yoo! Page 5. Android Mobile Application. Security Testing. Page 6 ...
 Mobile Application Security Testing
Mobile Application Security Testing
one-size-fits-all approach to mobile app security testing Developed a custom mobile app penetration testing set-up consisting of a device farm made up.
 2WTech
2WTech
iOS apps can store files in various formats such as PDF
 Testing Guide
Testing Guide
to guide to perform Web Application Penetration Testing. - Matteo. Meucci. OWASP thanks the many authors reviewers
 Penetration Testing - A hands-on introduction to Hacking.pdf
Penetration Testing - A hands-on introduction to Hacking.pdf
Nov 10 2015 The information in this book is distributed on an “As Is” basis
 Hands-On Mobile App Testing: A Guide for Mobile Testers and
Hands-On Mobile App Testing: A Guide for Mobile Testers and
Chapter 2: Introduction to Mobile Devices and Apps . . This book is a practical guide to mobile testing for anyone who works in the.
 XML Based Attacks
XML Based Attacks
Web/mobile application penetration tests. ? Internal network penetration tests. ? Curious about mobile and embedded devices. ? Bug bounty hunter.
 BUILDING A MOBILE APP PEN TESTING BLUEPRINT
BUILDING A MOBILE APP PEN TESTING BLUEPRINT
Books & Speaking. MOBILE SECURITY RESEARCH IS IN OUR DNA Pen tested thousands of mobile apps. Comprehensive experience and testing blueprint.
 ServiceNow Security Best Practice Guide
ServiceNow Security Best Practice Guide
Mobile application security . Vulnerability assessment and penetration testing . ... eBook. Certification. Description. Industry. Geography.
 [PDF] Mobile Application Penetration Testing
[PDF] Mobile Application Penetration Testing
Every effort has been made in the preparation of this book to ensure the accuracy of the information presented However the information contained in this book
 [PDF] Mobile Application Penetration Testing by Vijay Kumar Velu
[PDF] Mobile Application Penetration Testing by Vijay Kumar Velu
This book gives you the necessary skills to security test your mobile applications as a beginner developer or security practitioner You'll start by
 [PDF] Android Mobile Application Pentesting
[PDF] Android Mobile Application Pentesting
29 avr 2018 · Taken from learning pentesting for android device It is just a zip file First step into android mobile application penetration
 MOBILE APPLICATION PENETRATION TESTING BY VIJAY KUMAR
MOBILE APPLICATION PENETRATION TESTING BY VIJAY KUMAR
5 Explore real-world threat scenarios attacks on mobile applications and ways to counter them About This Book Gain insights into the current threat landscape
 Mobile Application Penetration Testing by Velu Vijay Kumar - Scribd
Mobile Application Penetration Testing by Velu Vijay Kumar - Scribd
11 mar 2016 · Explore real-world threat scenarios attacks on mobile applications and ways to counter them About This Book
 [PDF] Penetration Testing Ten Popular Swedish Android Applications - DiVA
[PDF] Penetration Testing Ten Popular Swedish Android Applications - DiVA
19 oct 2022 · OWASP's MSTG is manual which features procedures to test and verify compliance with requirements outlined in OWASP's Mobile Application Security
 [PDF] Penetration testing : a hands-on introduction to hacking - Zenk
[PDF] Penetration testing : a hands-on introduction to hacking - Zenk
10 nov 2015 · The information in this book is distributed on an “As Is” basis without warranty testing mobile hacking and exploit develop
 Mobile Application Penetration Testing - Packt
Mobile Application Penetration Testing - Packt
This book gives you the necessary skills to security test your mobile applications as a beginner developer or security practitioner
 Mobile Application Security Penetration Testing Based on OWASP
Mobile Application Security Penetration Testing Based on OWASP
28 mai 2020 · PDF Evolution of smartphones and smart devices affected one of the most used operating systems on smartphones and smart device is Android
 [PDF] Penetration Testing of Android-based Smartphones - CORE
[PDF] Penetration Testing of Android-based Smartphones - CORE
Research work on mobile operating systems began in 2000 and 2001 [7][8] which shows the security of memory protection permission-based file access control
How to test security testing in mobile application?
Use of SAST, DAST, and IAST techniques
Tools such as Klocwork and Checkmarx are useful for achieving SAST. Dynamic application security testing (DAST) focuses on a running app. DAST scan apps to check for any loopholes that may lead to security risks.What is mobile pentest vs web pentest?
Pentesting mobile apps requires additional permutation of testing strategies to think like hackers and test various platforms. On the other hand, web app pentesting is highly dependent on robust web browsers that involve testing real-time, simulated scenarios in various browsers on a remote network.What is the VAPT methodology of mobile application?
An android application is tested to identify any security flaws. This technique is known as Android VAPT. Decompiling, real-time analysis, and testing of the Android application under security conditions are all included.- DAST is a type of security testing that assesses the security of an application by testing it in its running state. This is in contrast to traditional penetration testing, which typically assesses the security of an application by testing it in a static state (in most cases).
PENETRATION TESTING
PENETRATION TESTING
A Hands-On Introduction
to HackingSan Francisco
by Georgia Weidman PENETRATION TESTING. Copyright © 2014 by Georgia Weidman. All rights reserved. No part of this work may be reproduced or transmitt ed in any form or by any means, electronic or mechanical, including photocopying, recording, or by any information storage or retrieval system, without the prior written permission of the copyright owner and the publisher.Printed in USA
First printing
18 17 16 15 14
1 2 3 4 5 6 7 8 9
ISBN-10: 1-59327-564-1
ISBN-13: 978-1-59327-564-8
Publisher: William Pollock
Production Editor: Alison Law
Cover Illustration: Mertsaloff/Shutterstock
Interior Design: Octopod Studios
Developmental Editor: William Pollock
Technical Reviewer: Jason Oliver
Copyeditor: Pamela Hunt
Compositor: Susan Glinert Stevens
Proofreader: James Fraleigh
Indexer: Nancy Guenther
For information on distribution, translations, or bulk sales, please con tact No Starch Press, Inc. directly:No Starch Press, Inc.
245 8th Street, San Francisco, CA 94103
phone: 415.863.9900; fax: 415.863.9950; info@nostarch.com; www.nostarch. com Library of Congress Cataloging-in-Publication DataWeidman, Georgia.
Penetration testing : a hands-on introduction to hacking / Georgia Wei dman. pages cmIncludes index.
ISBN 978-1-59327-564-8 (paperback) -- ISBN 1-59327-564-1 (paperback1. Penetration testing (Computer security) 2. Kali Linux. 3. Computer h
ackers. I. Title.QA76.9.A25W4258 2014
005.8'092--dc23
2014001066
No Starch Press and the No Starch Press logo are registered trademarks o f No Starch Press, Inc. Other product and company names mentioned herein may be the trademarks of their respective owners. Rather than use a trademark symbol with every occurrence of a trademarked name, we are using the nam es only in an editorial fashion and to the benefit of the trademark owner, with no intention of infringement of the trademark. The information in this book is distributed on an As Is" basis, w ithout warranty. While every precaution has been taken in the preparation of this work, neither the author nor No StarchPress, Inc. shall have any liability to any
person or entity with respect to any loss or damage caused or alleged to be caused directly or indirectly by the infor- mation contained in it.In memory of Jess Hilden
About the Author
Georgia Weidman is a penetration tester and
researcher, as well as the founder of BulbSecurity, a security consulting firm. She pre-
sents at conferences around the world includ- ing Black Hat, ShmooCon, and DerbyCon, and teaches classes on topics such as penetration testing, mobile hacking, and exploit develop- ment. Her work in mobile security has been featured in print and on television internation- ally. She was awarded a DARPA Cyber FastTrack grant to continue her work in mobile
device security.BRIEF CONTENTS
Foreword by Peter Van Eeckhoutte.........................................xixAcknowledgments
.xxv Chapter 0: Penetration Testing Primer........................................1PART I: THE BASICS
Chapter 1: Setting Up Your Virtual Lab.......................................9 Chapter 2: Using Kali Linux..............................................55Chapter 3: Programming
Chapter 4: Using the Metasploit Framework
..................................87PART II: ASSESSMENTS
Chapter 5: Information Gathering ........................................113 Chapter 6: Finding Vulnerabilities ........................................133 Chapter 7: Capturing Traffic............................................155PART III: ATTACKS
Chapter 8: Exploitation................................................179 Chapter 9: Password Attacks............................................197Chapter10: Client-Side Exploitation
Chapter 11: Social Engineering..........................................243 Chapter 12: Bypassing Antivirus Applications................................257 Chapter 13: Post Exploitation ...........................................277 Chapter 14: Web Application Testing .....................................313 Chapter 15: Wireless Attacks ...........................................339 viii Brief Contents chapter 16: a stack-based buffer overflow in linux ...........................361 chapter 17: a stack-based buffer overflow in windows ........................379 chapter 18: structured exception handler overwrites ..........................401 chapter 19: fuzzing, porting exploits, and metasploit modules....................421 chapter 20: using the smartphone pentest framework .........................445 resources indexCONTENTS IN DETAIL
FOREWORD by Peter Van Eeckhoutte xix
ACKNOWLEDGMENTS xxiii
INTRODUCTION xxv
A Note of Thanks..................................................xxvi About This Book.................................................. .xxvi Part I: The Basics...........................................xxviiPart II: Assessments
. . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . xxviiPart III: Attacks
Part IV: Exploit Development.................................. .xxviiiPart V: Mobile Hacking
0PENETRATION
TESTING PRIMER 1
The Stages of the Penetration Test .......................................2Pre-engagement
Information Gathering.........................................4 Threat Modeling.............................................4Vulnerability Analysis
Exploitation
Post Exploitation
Reporting
Summary
PART I
THE BASICS
1SETTING UP YOUR VIRTUAL LAB 9
Installing VMware ..................................................9Setting Up Kali Linux
Configuring the Network for Your Virtual Machine
....................13 Installing Nessus............................................17 Installing Additional Software...................................20Setting Up Android Emulators
..................................22 Smartphone Pentest Framework..................................27Target Virtual Machines
Creating the Windows XP Target.......................................29VMware Player on Microsoft Windows
............................29 VMware Fusion on Mac OS....................................31Installing and Activating Windows
...............................32 x Contents in Detail Installing VMware Tools.......................................35Turning Off Windows Firewall
..................................37Setting User Passwords
Setting a Static IP Address
.....................................38 Making XP Act Like It"s a Member of a Windows Domain ...............39 Installing Vulnerable Software...................................40Installing Immunity Debugger and Mona
...........................46Setting Up the Ubuntu 8
.10 Target......................................48 Creating the Windows 7 Target........................................48Creating a User Account
......................................48 Opting Out of Automatic Updates................................50Setting a Static IP Address
.....................................51Adding a Second Network Interface
..............................52 Installing Additional Software...................................52Summary
Linux Command Line ...............................................56The Linux Filesystem
Changing Directories.........................................56 Learning About Commands: The Man Pages...............................57 User Privileges....................................................58Adding a User
Adding a User to the sudoers File
................................59 Switching Users and Using sudo.................................59Creating a New File or Directory
................................60Copying, Moving, and Removing Files
............................60 Adding Text to a File.........................................61Appending Text to a File
......................................61File Permissions
Editing Files......................................................62 Searching for Text...........................................63Editing a File with vi
Data Manipulation.................................................64 Using grep................................................65 Using sed.................................................65 Pattern Matching with awk.....................................66Managing Installed Packages
Processes and Services..............................................67 Managing Networking..............................................67Setting a Static IP Address
.....................................68Viewing Network Connections
..................................69 Netcat: The Swiss Army Knife of TCP/IP Connections.........................69Check to See If a Port Is Listening
................................70 Opening a Command Shell Listener...............................70Pushing a Command Shell Back to a Listener
........................71Automating Tasks with cron Jobs
Summary
Contents in Detail xi
3PROGRAMMING
754
USING THE METASPLOIT FRAMEWORK 87
xii Contents in DetailPART II
ASSESSMENTS
5INFORMATION GATHERING 113
6FINDING VU
LNERABILITIES 133
7 CAPTURING TRAFFIC 155
Contents in Detail xiiiARP Cache Poisoning..............................................160 ARP Basics...............................................161 IP Forwarding.............................................163 ARP Cache Poisoning with Arpspoof.............................164 Using ARP Cache Poisoning to Impersonate the Default Gateway . . . . . . . . . 165DNS Cache Poisoning
Getting Started............................................168 Using Dnsspoof............................................169SSL Attacks
SSL Basics ...............................................170Using Ettercap for SSL Man-in-the-Middle Attacks
....................171 SSL Stripping....................................................173 Using SSLstrip.............................................174Summary
Revisiting MS08-067 ..............................................180Metasploit Payloads
Meterpreter
Exploiting WebDAV Default Credentials.................................182Running a Script on the Target Web Server
........................183 Uploading a Msfvenom Payload................................183Exploiting Open phpMyAdmin
Downloading a File with TFTP..................................187Downloading Sensitive Files
Downloading a Configuration File...............................188Downloading the Windows SAM
...............................189 Exploiting a Buffer Overflow in Third-Party Software.........................190 Exploiting Third-Party Web Applications.................................191 Exploiting a Compromised Service.....................................193 Exploiting Open NFS Shares.........................................194Summary
Password Management.............................................197 Online Password Attacks............................................198Guessing Usernames and Passwords with Hydra
....................202 Offline Password Attacks............................................203 Recovering Password Hashes from a Windows SAM File...............204 Dumping Password Hashes with Physical Access.....................206 LM vs . NTLM Hashing Algorithms ...............................208 The Trouble with LM Password Hashes............................209 xiv Contents in Detail John the Ripper............................................210Cracking Linux Passwords
....................................212Cracking Configuration File Passwords
...........................212Rainbow Tables
Online Password-Cracking Services..............................213 Dumping Plaintext Passwords from Memory with Windows Credential Editor .......213Summary
Bypassing Filters with Metasploit Payloads ...............................216 All Ports.................................................216HTTP and HTTPS Payloads
....................................217 Client-Side Attacks................................................218Browser Exploitation
PDF Exploits..............................................225 Java Exploits..............................................230 Winamp ................................................237Summary
The Social-Engineer Toolkit ..........................................244Spear-Phishing Attacks
Choosing a Payload
Setting Options............................................247Naming Your File
Single or Mass Email........................................247Creating the Template
. . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . 248Setting the Target
Setting Up a Listener
Web Attacks....................................................250Mass Email Attacks
Multipronged Attacks
Summary
Msfvenom
How Antivirus Applications Work
.....................................260Microsoft Security Essentials
VirusTotal
quotesdbs_dbs14.pdfusesText_20[PDF] mobile application performance testing tools
[PDF] mobile application reference architecture
[PDF] mobile application security pdf
[PDF] mobile application security ppt
[PDF] mobile application security testing approach
[PDF] mobile application security testing checklist
[PDF] mobile application security testing pdf
[PDF] mobile application security testing ppt
[PDF] mobile application testing checklist xls
[PDF] mobile apps for language learning pdf
[PDF] mobile computing applications
[PDF] mobile computing architecture
[PDF] mobile computing framework
[PDF] mobile computing functions pdf
